Notes from "The Lean Startup: How Today’s Entrepreneurs Use Continuous Innovation to Create Radically Successful Businesses"
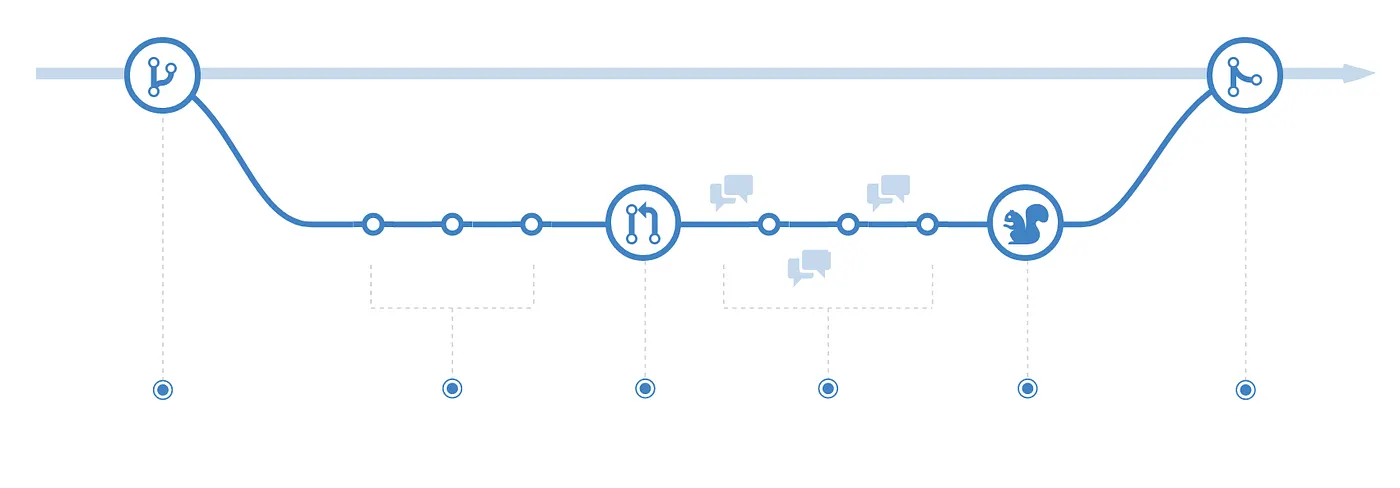
Lean Startup is about quickly building a simple version of a concept, testing it with real users, learning from the results, and improving quickly to reduce the wastage of time and resources.